Table of Contents
OpenWRT on Linksys WRT54G How-to
- Cette page décrit l'installation d'OpenWRT sur un routeur Linksys WRT54G fraîchement acquis. La manip' décrite consiste à remplacer le firmware d'origine par une version Libre qui apporte au routeur les mêmes fonctionnalités.
- Le matériel utilisé est un routeur Linksys WRT54G version 3.1 avec une firmware d'origine 4.01.1.
- La version d'OpenWRT installée est la RC3 avec le firmware openwrt-wrt54g-squashfs.bin.
- La documentation officielle est d'une aide précieuse et il est fortement conseillée de la lire avant de se lancer dans l'installation, section Troubleshooting incluse.
Avertissements
 Installer OpenWRT sur un routeur Linksys annule toutes les garanties qui accompagnent le produit neuf. Le principal inconvénient est que vous vous retrouverez donc sans recours en cas de problème (en dehors des forums et listes OpenWRT). L'avantage est que vous pourrez en profiter pour démonter le routeur et voir ce qu'il a dans le coffre… Vous voici prévenu(e)s !
Installer OpenWRT sur un routeur Linksys annule toutes les garanties qui accompagnent le produit neuf. Le principal inconvénient est que vous vous retrouverez donc sans recours en cas de problème (en dehors des forums et listes OpenWRT). L'avantage est que vous pourrez en profiter pour démonter le routeur et voir ce qu'il a dans le coffre… Vous voici prévenu(e)s ! 
 N'oubliez pas : le WRT54G est une “petite” machine dont l'espace disque oscille entre 4 et 8 Mo selon les modèles. Il ne faut donc pas espérer y installer beaucoup plus que le minimum. Une utilisation (très) courante consiste à l'utiliser comme… AP Wifi ! Si vous devez/voulez journaliser, il faut envisager - plus que sérieusement - d'utiliser pour cela un démon syslog sur une machine à part.
N'oubliez pas : le WRT54G est une “petite” machine dont l'espace disque oscille entre 4 et 8 Mo selon les modèles. Il ne faut donc pas espérer y installer beaucoup plus que le minimum. Une utilisation (très) courante consiste à l'utiliser comme… AP Wifi ! Si vous devez/voulez journaliser, il faut envisager - plus que sérieusement - d'utiliser pour cela un démon syslog sur une machine à part.
Le routeur Linksys WRT54G
- Le routeur WRT54G est un boitier “trois en un” qui fournit une connectivité sans fil (802.11b et 802.11g) et Ethernet 10/100 Mbits ainsi que la fonction routeur qui permet à tout ce beau monde d'être connecté à l'Internet par le biais, par exemple, d'une liaison ADSL.
- Les fonctionnalités DHCP et pare-feu à état ainsi qu'une interface d'administration HTTP/HTTPS alliées à un très bon prix achèvent de faire de ce produit un bon achat.
- Enfin, et c'est que qui nous intéresse dans cet article, le routeur WRT54G est la plate-forme de choix pour tester des firmware Libre au premier rang desquels on trouve OpenWRT.
OpenWRT
- OpenWRT est une distribution Linux pour routeurs Wifi. Elle fournit les fonctionnalités de base nécessaires à ce type d'appareil ainsi qu'un environnement minimaliste qui permet d'étendre les capacités du routeur à l'aide de paquetages.
Installation en 3 étapes
Etape 1
- Première étape : lecture de la documentation officielle : Site OpenWRT
- Une fois l'obscur objet du désir acheté (61 euros sur Amazon), livré et déballé, il faut activer la fonctionnalité boot_wait. En gros, cela consiste à induire un délai de 5 secondes au boot du routeur. Ces 5 précieuses secondes permettent de charger le firmware depuis un serveur TFTP. Par firmware, il faut comprendre les mises à jour du logiciel Linksys mais aussi - et surtout dans notre cas - OpenWRT.
Activation du boot_wait
- Note On trouve ici ou là des modes opératoires qui préconisent de downgrader le firmware du routeur si sa version est supérieure à 3.7 sous peine de ne pouvoir exploiter le “bug” du ping. Dans mon cas, le routeur a été livré avec un firmware en version 4.01.1 et tout a fonctionné. La documentation officielle précise de surcroît que l'exploitation du bug n'est pas liée à une version de firmware.
- Il est impératif d'affecter à l'interface Internet du routeur une adresse IP. Le plus simple est encore d'utiliser une adresse quelconque en statique. Attention : il faut renseigner aussi le netmask et la passerelle (gateway).
- Il faut ensuite ouvrir la fenêtre Ping (menu Diagnostics) et entrer l'une après l'autre les lignes suivantes en cliquant sur le bouton Ping après chaque entrée :
;cp${IFS}*/*/nvram${IFS}/tmp/n
;*/n${IFS}set${IFS}boot_wait=on
;*/n${IFS}commit
;*/n${IFS}show>tmp/ping.log
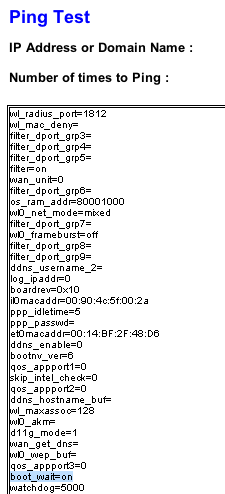
Si tout c'est bien passé, l'écran de diagnostic se présente sous la forme suivante et l'option boot_wait apparait à on :
Etape 2
- Télécharger la version courante d'OpenWRT.
- Utiliser un client TFTP pour télécharger le firmware OpenWRT sur le routeur.
- Note Pour une découverte d'OpenWRT, il est prudent de choisir squashfs comme système de fichier. C'est la méthode standard, dixit la doc. officielle.
- Une fois le transfert effectué, laissez le routeur booter. Cela peut prendre quelques minutes. Pour suivre la progression du démarrage, surveillez la LED DMZ : elle est allumée durant le boot, éteinte dès que le système est “up”.
Etape 3
- Lorsque la phase de boot est terminée, vérifiez que tout c'est bien passé en ouvrant une session telnet sur l'IP 192.168.1.1 (IP utilisée par défaut) :
bash-2.05a$ telnet 192.168.1.1
Trying 192.168.1.1...
Connected to 192.168.1.1.
Escape character is '^]'.
=== IMPORTANT ============================
Use 'passwd' to set your login password
this will disable telnet and enable SSH
------------------------------------------
BusyBox v1.00 (2005.09.14-15:55+0000) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
WHITE RUSSIAN (RC3) -------------------------------
* 2 oz Vodka Mix the Vodka and Kahlua together
* 1 oz Kahlua over ice, then float the cream or
* 1/2oz cream milk on the top.
---------------------------------------------------
root@linksys:/#
- Voilà, OpenWRT tourne maintenant sur votre routeur, et vice versa.
Firstboot
- Le firmware OpenWRT est composé d'un noyau et d'un système de fichiers en lecture seule : squashfs.
- Au démarrage du routeur, une partition jffs2 est automatiquement (enfin, quand tout se passe bien…) créée et montée en mode écriture/lecture. La création de cette partition est réalisée par le script firstboot.
- Avant l'exécution de ce script, voici l'état des partitions (snapshot réalisé en mode failsafe que nous aborderons plus loin) :
root@linksys:/# mount /dev/root on / type squashfs (ro) none on /dev type devfs (rw) none on /proc type proc (rw) none on /tmp type tmpfs (rw,nosuid,nodev) none on /dev/pts type devpts (rw)
- Après exécution du script firstboot :
root@linksys:/etc# mount /dev/root on /rom type squashfs (ro) none on /rom/dev type devfs (rw) none on /rom/tmp type tmpfs (rw,nosuid,nodev) none on /rom/dev/pts type devpts (rw) /dev/mtdblock/4 on / type jffs2 (rw) none on /proc type proc (rw) none on /dev type devfs (rw) none on /tmp type ramfs (rw)
- L'espace “disque” total est de 8 Mo répartis comme ceci :
root@linksys:/# df -h Filesystem Size Used Available Use% Mounted on /dev/root 1.1M 1.1M 0 100% /rom none 7.0M 4.0k 7.0M 0% /rom/tmp /dev/mtdblock/4 2.2M 360.0k 1.8M 16% /
Note La partition /rom est en lecture seule et de type squashfs. Comme nous le constaterons plus loin, de nombreux fichiers de configuration de base du répertoire /etc sont des liens vers des fichiers localisés sur cette partition. De ce fait, ils ne sont pas éditables et il est nécessaire d'effacer le lien et de créer un fichier dans le répertoire /etc pour manipuler les paramètres de certains programmes.
- La commande dmesg fournit les informations suivantes :
root@linksys:/# dmesg CPU revision is: 00029007 Primary instruction cache 8kB, physically tagged, 2-way, linesize 16 bytes. Primary data cache 4kB, 2-way, linesize 16 bytes. Linux version 2.4.30 (wbx@ux-2y01) (gcc version 3.4.4) #1 Wed Sep 14 17:49:26 CEST 2005 Setting the PFC value as 0x15 Determined physical RAM map: memory: 01000000 @ 00000000 (usable) On node 0 totalpages: 4096 zone(0): 4096 pages. zone(1): 0 pages. zone(2): 0 pages. Kernel command line: root=/dev/mtdblock2 rootfstype=squashfs,jffs2 init=/etc/preinit noinitrd console=ttyS0,115200 CPU: BCM4712 rev 2 at 216 MHz Using 108.000 MHz high precision timer. Calibrating delay loop... 215.44 BogoMIPS Memory: 14296k/16384k available (1390k kernel code, 2088k reserved, 100k data, 80k init, 0k highmem) Dentry cache hash table entries: 2048 (order: 2, 16384 bytes) Inode cache hash table entries: 1024 (order: 1, 8192 bytes) Mount cache hash table entries: 512 (order: 0, 4096 bytes) Buffer cache hash table entries: 1024 (order: 0, 4096 bytes) Page-cache hash table entries: 4096 (order: 2, 16384 bytes) Checking for 'wait' instruction... unavailable. POSIX conformance testing by UNIFIX PCI: Disabled PCI: Fixing up bus 0 Linux NET4.0 for Linux 2.4 Based upon Swansea University Computer Society NET3.039 Initializing RT netlink socket Starting kswapd devfs: v1.12c (20020818) Richard Gooch (rgooch@atnf.csiro.au) devfs: boot_options: 0x1 JFFS2 version 2.1. (C) 2001 Red Hat, Inc., designed by Axis Communications AB. Squashfs 2.1-r2 (released 2004/12/15) (C) 2002-2004 Phillip Lougher pty: 256 Unix98 ptys configured Serial driver version 5.05c (2001-07-08) with MANY_PORTS SHARE_IRQ SERIAL_PCI enabled ttyS00 at 0xb8000300 (irq = 3) is a 16550A ttyS01 at 0xb8000400 (irq = 0) is a 16550A Software Watchdog Timer: 0.05, timer margin: 60 sec Physically mapped flash: Found an alias at 0x400000 for the chip at 0x0 Physically mapped flash: Found an alias at 0x800000 for the chip at 0x0 Physically mapped flash: Found an alias at 0xc00000 for the chip at 0x0 Physically mapped flash: Found an alias at 0x1000000 for the chip at 0x0 Physically mapped flash: Found an alias at 0x1400000 for the chip at 0x0 Physically mapped flash: Found an alias at 0x1800000 for the chip at 0x0 Physically mapped flash: Found an alias at 0x1c00000 for the chip at 0x0 cfi_cmdset_0001: Erase suspend on write enabled 0: offset=0x0,size=0x2000,blocks=8 1: offset=0x10000,size=0x10000,blocks=63 Using word write method Flash device: 0x400000 at 0x1c000000 Creating 5 MTD partitions on "Physically mapped flash": 0x00000000-0x00040000 : "pmon" 0x00040000-0x003f0000 : "linux" 0x000ba4b0-0x001c0000 : "rootfs" mtd: partition "rootfs" doesn't start on an erase block boundary -- force read-only 0x003f0000-0x00400000 : "nvram" 0x001c0000-0x003f0000 : "OpenWrt" Initializing Cryptographic API NET4: Linux TCP/IP 1.0 for NET4.0 IP Protocols: ICMP, UDP, TCP, IGMP IP: routing cache hash table of 512 buckets, 4Kbytes TCP: Hash tables configured (established 1024 bind 2048) ip_conntrack version 2.1 (5953 buckets, 5953 max) - 320 bytes per conntrack ip_tables: (C) 2000-2002 Netfilter core team NET4: Unix domain sockets 1.0/SMP for Linux NET4.0. NET4: Ethernet Bridge 008 for NET4.0 802.1Q VLAN Support v1.8 Ben Greear <greearb@candelatech.com> All bugs added by David S. Miller <davem@redhat.com> VFS: Mounted root (squashfs filesystem) readonly. Mounted devfs on /dev Freeing unused kernel memory: 80k freed Algorithmics/MIPS FPU Emulator v1.5 diag boardtype: 00000708 jffs2.bbc: SIZE compression mode activated. PCI: Setting latency timer of device 00:02.0 to 64 eth0: Broadcom BCM47xx 10/100 Mbps Ethernet Controller 3.90.23.0 PCI: Setting latency timer of device 00:01.0 to 64 eth1: Broadcom BCM4320 802.11 Wireless Controller 3.90.37.0 device eth0 entered promiscuous mode vlan0: Setting MAC address to 00 14 bf 2f 48 d6. VLAN (vlan0): Underlying device (eth0) has same MAC, not checking promiscious mode. vlan0: add 01:00:5e:00:00:01 mcast address to master interface device eth1 entered promiscuous mode eth1: attempt to add interface with same source address. br0: port 2(eth1) entering learning state br0: port 1(vlan0) entering learning state br0: port 2(eth1) entering forwarding state br0: topology change detected, propagating br0: port 1(vlan0) entering forwarding state br0: topology change detected, propagating vlan1: Setting MAC address to 00 14 bf 2f 48 d7. vlan1: add 01:00:5e:00:00:01 mcast address to master interface
- Note Le script firstboot peut également être utilisé pour réinitialiser OpenWRT, ce qui revient à effacer toutes les modifications apportées précédemment : fichiers modifiés, mais également paquetages installés. Il est ainsi possible de revenir à l'état initial d'après installation avec les valeurs et objets (fichiers, paquetages) par défaut.
Découverte du système
- Par défaut, nous venons de le voir, la connexion se fait en telnet sans mot de passe. Avant de sécuriser a minima l'administration de notre routeur en activant SSH, faisons un rapide petit tour du propriétaire.
- OpenWRT fournit un noyau Linux 2.4 :
root@linksys:/# uname -a Linux linksys 2.4.30 #1 Wed Sep 14 17:49:26 CEST 2005 mips unknown
un shell (ash) et les paquetages de base qui permettent d'activer la fonctionnalité AP WiFi :
root@linksys:/# ipkg list base-files - 2 - base-files-brcm - 1 - bridge - 1.0.6-1 - busybox - 1.00-2 - dnsmasq - 2.22-2 - dropbear - 0.45-3 - hotplug - 2 - ipkg - 0.99.149-2 - iptables - 1.3.1-1 - kernel - 2.4.30-brcm-2 - kmod-brcm-et - 2.4.30-brcm-2 - kmod-brcm-wl - 2.4.30-brcm-2 - kmod-diag - 2.4.30-brcm-2 - kmod-ppp - 2.4.30-brcm-2 - kmod-pppoe - 2.4.30-brcm-2 - kmod-wlcompat - 2.4.30-brcm-3 - libgcc - 3.4.4-2 - mtd - 2 - nvram - 1 - ppp - 2.4.3-6 - ppp-mod-pppoe - 2.4.3-6 - uclibc - 0.9.27-2 - wificonf - 4 - wireless-tools - 28.pre7-1 - zlib - 1.2.2-2 - Successfully terminated.
L'utilitaire ipkg est un gestionnaire de paquetages OpenWRT. L'option list utilisée ci-dessus, comme son nom l'indique, affiche la liste des paquetages installés en standard. Outre l'utilitaire ipkg, on notera la présence du filtre de paquets iptables et de dropbear, un serveur SSH2 pour OpenWRT.
- ash est quant à lui un shell tout particulièrement adapté aux environnements restreints car il est peu gourmand en mémoire et tient peu de place sur disque. Il vise une compatibilité maximale avec le Bourne Shell.
Configuration Réseau
- Le routeur WRT54G possède plusieurs interfaces physiques : 1 interface Ethernet dite “WAN” ou Internet, 4 interfaces Ethernet dites “LAN” et une interface Wifi.
- la commande ifconfig fait ressortir les interfaces logiques suivantes :
root@linksys:/etc/openvpn# ifconfig
br0 Link encap:Ethernet HWaddr 00:14:BF:2F:48:D6
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8372 errors:0 dropped:0 overruns:0 frame:0
TX packets:7629 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1546676 (1.4 MiB) TX bytes:1439167 (1.3 MiB)
eth0 Link encap:Ethernet HWaddr 00:14:BF:2F:48:D6
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:8372 errors:0 dropped:0 overruns:0 frame:0
TX packets:7629 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1730860 (1.6 MiB) TX bytes:1469683 (1.4 MiB)
Interrupt:5 Base address:0x2000
eth1 Link encap:Ethernet HWaddr 00:14:BF:2F:48:D6
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:11480
TX packets:375 errors:118 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:30381 (29.6 KiB)
Interrupt:4 Base address:0x1000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:9899 errors:0 dropped:0 overruns:0 frame:0
TX packets:9899 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:963498 (940.9 KiB) TX bytes:963498 (940.9 KiB)
vlan0 Link encap:Ethernet HWaddr 00:14:BF:2F:48:D6
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8372 errors:0 dropped:0 overruns:0 frame:0
TX packets:7629 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1580164 (1.5 MiB) TX bytes:1469683 (1.4 MiB)
vlan1 Link encap:Ethernet HWaddr 00:14:BF:2F:48:D7
inet addr:213.223.10.10 Bcast:213.223.10.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
- L'interface WAN apparait sous le nom vlan1.
- Les 4 interfaces LAN et l'interface Wifi (eth1) sont quant à elles regroupées (bridgées) autour de l'interface br0 sur le réseau 192.168.1.0/24. L'adresse IP d'administration du routeur sur ce réseau est 192.168.1.1. L'attriburion d'IP sur ce réseau se fait à l'aide d'un serveur DHCP qui tourne sur le routeur.
Gestion de la NVRAM
- La quasi totalité des paramètres de configuration du routeur sont stockés de manière non volatile sur la NVRAM.
- La manipulation de ces paramètres s'effectue à l'aide de la commande nvram qui permet de lister l'ensemble des paramètres et la valeur de chacun d'eux et de les modifier. Dans l'exemple ci-dessous, nous affichons l'ensemble des paramètres relatifs à l'interface Wifi :
root@linksys:~# nvram show | grep wl0 wl0_net_mode=mixed wl0_frameburst=off wl0_wep_buf= wl0_akm= wl0_macmode1=disabled wl0_infra=1 wl0_country_code=ALL wl0_wme_sta_be=15 1023 3 0 0 off wl0_ifname=eth1 wl0_wme_sta_bk=15 1023 7 0 0 off wl0_mrate=0 wl0_mode=ap wl0_ap_isolate=0 wl0_gmode=1 wl0_wme_no_ack=off wl0_wep_last= wl0_ssid=linksys wl0_dtim=1 wl0id=0x4320 wl0_key1= wl0_key2= wl0_key3= wl0_key4= wl0_wme_ap_vi=7 15 1 6016 3008 off wl0_closed=1 wl0_rate=0 wl0_plcphdr=long wl0_macmode=disabled wl0_radioids=BCM2050 wl0_wme_ap_vo=3 7 1 3264 1504 off wl0gpio2=0 wl0_phytype=g wl0gpio3=0 wl0_lazywds=1 wl0_afterburner=off wl0_antdiv=-1 wl0_wpa_psk= wl0_mac_list= wl0_unit=0 wl0_net_reauth=36000 wl0_wds= wl0_mac_deny= wl0_auth=0 wl0_wme=off wl0_radius_port=1812 wl0_radius_ipaddr= wl0_wme_sta_vi=7 15 2 6016 3008 off wl0_wme_sta_vo=3 7 2 3264 1504 off wl0_maxassoc=128 wl0_phytypes=g wl0_wep=disabled wl0_frag=2346 wl0_country=ALL wl0_rateset=default wl0_wep_bit=64 wl0_passphrase= wl0_rts=2347 wl0_wpa_gtk_rekey=3600 wl0_key=1 wl0_active_mac= wl0_radio=0 wl0_bcn=100 wl0_hwaddr=00:14:BF:2F:48:D8 wl0_wep_gen= wl0_gmode_protection=off wl0_maclist= wl0_radius_key= wl0_wme_ap_be=15 63 3 0 0 off wl0_corerev=7 wl0_channel=11 wl0_wds_timeout=1 wl0_wme_ap_bk=15 1023 7 0 0 off wl0_auth_mode=none wl0_crypto=tkip
Pour modifier un paramètre :
: Exemple : désactiver le wifi # nvram set wl0_radio=0 : "flasher" la nouvelle valeur # nvram commit : Et l'inévitable reboot pour la prise en compte : du nouveau paramètre # reboot
Adieu telnet, bonjour SSH
- Tout fonctionne bien, il est maintenant temps de passer aux choses plus sérieuses, à commencer par sécuriser le mode d'administration du routeur. Nous allons pour cela activer le serveur SSH Dropbear fourni en standard et stopper le démon telnet.
- Il faut savoir que même si le démon ssh est lancé, aucune connexion SSH root ne sera possible si cet utilisateur n'a pas de mot de passe (ca qui est le cas par défaut).
- Il faut donc en premier lieu affecter un mot de passe à l'utilisateur root. Nous sommes sur un Unix-like, la commande passwd fait donc très bien l'affaire.
- Un kill sur le processus telnetd réduira ce dernier au silence. Pour pérenniser cette situation, il faudra aussi effacer le lien symbolique /etc/init.d/S50telnet.
- Il sera toujours possible pour les plus exigeants de remplacer DropBear pour un serveur OpenSSH. Des paquetages existent pour cela.
Installation de paquetages
- Les fonctionnalités de base d'OpenWRT peuvent (relativement) aisément étendues à l'aide de paquetages.
- L'utilitaire ipkg déjà cité plus haut est alors utilisé. Dans l'exemple ci-dessous, nous avons ainsi installé la bibliothèque libpcap et tcpdump :
root@linksys:~# ipkg install libpcap_0.8.3-1_mipsel.ipk Installing libpcap (0.8.3-1) to root... Configuring libpcap Successfully terminated. root@linksys:~# ipkg install tcpdump_3.8.3-1_mipsel.ipk Installing tcpdump (3.8.3-1) to root... Configuring tcpdump Successfully terminated.
- L'espace disque étant limité, il est intéressant de noter qu'il est possible - et souhaitable - d'installer des paquetages depuis un site web plutôt qu'importer les paquetages sur le routeur (comme dans l'exemple ci-dessus). Pour cela, il faut éditer le fichier /etc/ipkg.conf pour spécifier l'adresse du site que l'on veut utiliser comme source.
- Dans le mode d'installation standard (squashfs), les principaux fichiers du répertoire /etc sont en réalité des liens vers leurs homologues de la partition /rom :
root@linksys:~# ls -l /etc lrwxrwxrwx 1 root root 15 Jan 1 02:15 banner -> /rom/etc/banner lrwxrwxrwx 1 root root 21 Jan 1 02:15 dnsmasq.conf -> /rom/etc/dnsmasq.conf drwxr-xr-x 1 root root 0 Jan 1 00:04 dropbear lrwxrwxrwx 1 root root 22 Jan 1 02:15 firewall.user -> /rom/etc/firewall.user lrwxrwxrwx 1 root root 21 Jan 1 02:15 functions.sh -> /rom/etc/functions.sh lrwxrwxrwx 1 root root 14 Jan 1 02:15 group -> /rom/etc/group lrwxrwxrwx 1 root root 14 Jan 1 02:15 hosts -> /rom/etc/hosts drwxr-xr-x 1 root root 0 Jan 1 02:15 init.d lrwxrwxrwx 1 root root 16 Jan 1 02:15 inittab -> /rom/etc/inittab -rw-r----- 1 root root 167 Jan 1 01:36 ipkg.conf lrwxrwxrwx 1 root root 16 Jan 1 02:15 modules -> /rom/etc/modules drwxr-xr-x 1 root root 0 Jan 1 02:15 modules.d lrwxrwxrwx 1 root root 24 Jan 1 02:15 nvram.overrides -> /rom/etc/nvram.overrides -rw-r----- 1 root root 99 Jan 1 00:01 passwd -rw------- 1 root root 74 Aug 13 2005 passwd- drwxr-xr-x 1 root root 0 Jan 1 02:15 ppp lrwxrwxrwx 1 root root 16 Jan 1 02:15 preinit -> /rom/etc/preinit lrwxrwxrwx 1 root root 16 Jan 1 02:15 profile -> /rom/etc/profile lrwxrwxrwx 1 root root 18 Jan 1 02:15 protocols -> /rom/etc/protocols lrwxrwxrwx 1 root root 20 Jan 1 02:15 resolv.conf -> /rom/etc/resolv.conf lrwxrwxrwx 1 root root 15 Jan 1 02:15 shells -> /rom/etc/shells lrwxrwxrwx 1 root root 16 Jan 1 02:15 sysconf -> /rom/etc/sysconf lrwxrwxrwx 1 root root 20 Jan 1 02:15 sysctl.conf -> /rom/etc/sysctl.conf
Or cette partition de type squashfs est en lecture seule (les plus perspicaces auront deviné que ROM signifie Read Only Memory) :
root@linksys:~# mount /dev/root on /rom type squashfs (ro) none on /rom/dev type devfs (rw) /dev/mtdblock/4 on / type jffs2 (rw) none on /proc type proc (rw) none on /dev type devfs (rw) none on /tmp type tmpfs (rw,nosuid,nodev) none on /dev/pts type devpts (rw)
- Pour modifier le fichier original /etc/ipkg.conf, il convient d'effectuer les petites modifications suivantes :
rm /etc/ipkg.conf cp /rom/etc/ipkg.conf /etc/ipkg.conf
Le fichier est alors créé sur une partition en lecture/écriture et peut être modifié sans problème.
- Cette remarque et cette méthode s'appliquent à tous les liens contenus dans le répertoire /etc.
- Parmi les paquetages à installer rapidement : openntpd et htpdate pour automatiser la mise à jour de l'horloge système du routeur. Sans ces outils, vous êtes condamnés à perdre la date système à chaque arrêt du routeur.
Installation d'une interface graphique
- Les inconditionnels de la GUI regretteront sûrement d'avoir dû troquer l'interface Web d'origine pour l'administration à la main via SSH.
- Qu'ils se consolent : il existe plusieurs projets - plus ou moins aboutis et complets - d'interface graphique pour OpenWRT.
- Dans ce paragraphe, nous décrirons l'installation d'une des interfaces les plus prometteuses à notre goût (jugement cependant tout à fait subjectif et donc à prendre comme tel !) : OpenWRT Administrative Console.
- Cet outil utilise le serveur HTTP livré en standard avec openWRT et est constitué de scripts qui appellent majoritairement l'utilitaire nvram décrit ci-dessus pour modifier à la volée les paramètres de configuration réseau du routeur.
- Elle permet ainsi de modifier la configuration des interfaces réseau du routeur mais elle permet aussi de gérer les paquetages (mise à jour, ajoût, destruction).
- Il faut installer deux paquetages : haserl et webif-test.
- Le résultat est illustré par les quelques captures suivantes :
- Une version de démonstration complète en ligne est disponible ici.
Filtrage réseau
- Par défaut, OpenWRT fournit un ensemble de règles IPtables pour appliquer un filtrage réseau minimaliste mais très bien adapté à un usage “domestique” du routeur.
- En gros, les flux sortants sont autorisés et l'activation du filtrage à état (stateful inspection) garantit que seuls les flux retour sont acceptés.
- Voici le fichier de règles inclus en standard et chargé au démarrage :
root@point-central:~# more /etc/init.d/S45firewall
#!/bin/sh
## Please make changes in /etc/firewall.user
${FAILSAFE:+exit}
. /etc/functions.sh
WAN=$(nvram get wan_ifname)
LAN=$(nvram get lan_ifname)
## CLEAR TABLES
for T in filter nat mangle; do
iptables -t $T -F
iptables -t $T -X
done
iptables -N input_rule
iptables -N output_rule
iptables -N forwarding_rule
iptables -t nat -N prerouting_rule
iptables -t nat -N postrouting_rule
### INPUT
### (connections with the router as destination)
# base case
iptables -P INPUT DROP
iptables -A INPUT -m state --state INVALID -j DROP
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --tcp-flags SYN SYN --tcp-option \! 2 -j DROP
#
# insert accept rule or to jump to new accept-check table here
#
iptables -A INPUT -j input_rule
# allow
iptables -A INPUT -i \! $WAN -j ACCEPT # allow from lan/wifi interfaces
iptables -A INPUT -p icmp -j ACCEPT # allow ICMP
iptables -A INPUT -p gre -j ACCEPT # allow GRE
# reject (what to do with anything not allowed earlier)
iptables -A INPUT -p tcp -j REJECT --reject-with tcp-reset
iptables -A INPUT -j REJECT --reject-with icmp-port-unreachable
### OUTPUT
### (connections with the router as source)
# base case
iptables -P OUTPUT DROP
iptables -A OUTPUT -m state --state INVALID -j DROP
iptables -A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
#
# insert accept rule or to jump to new accept-check table here
#
iptables -A OUTPUT -j output_rule
# allow
iptables -A OUTPUT -j ACCEPT #allow everything out
# reject (what to do with anything not allowed earlier)
iptables -A OUTPUT -p tcp -j REJECT --reject-with tcp-reset
iptables -A OUTPUT -j REJECT --reject-with icmp-port-unreachable
### FORWARDING
### (connections routed through the router)
# base case
iptables -P FORWARD DROP
iptables -A FORWARD -m state --state INVALID -j DROP
iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
#
# insert accept rule or to jump to new accept-check table here
#
iptables -A FORWARD -j forwarding_rule
# allow
iptables -A FORWARD -i br0 -o br0 -j ACCEPT
iptables -A FORWARD -i $LAN -o $WAN -j ACCEPT
# reject (what to do with anything not allowed earlier)
# uses the default -P DROP
### MASQ
iptables -t nat -A PREROUTING -j prerouting_rule
iptables -t nat -A POSTROUTING -j postrouting_rule
iptables -t nat -A POSTROUTING -o $WAN -j MASQUERADE
## USER RULES
[ -f /etc/firewall.user ] && . /etc/firewall.user
En cas de problème...
- La vie n'est pas toujours un long fleuve tranquille et il peut être utile de savoir comment se sortir de quelques mauvais pas tels que connexion impossible au routeur ou blocage suite à une lecture trop rapide de la documentation officielle (ça sent le vécu, n'est-ce pas ?
 ).
). - Premier secours : booter le routeur en mode failsafe (équivalent à un bon vieux boot single). Pour cela, il faut débrancher le routeur puis le rallumer. Dès que la LED DMZ s'allume, il faut presser durant 2 secondes le bouton Reset situé à l'arrière de l'appareil. Si l'opération se déroule bien, la LED DMZ clignotte alors trois fois et la procédure de boot continue. La connexion au routeur par telnet est alors possible. Le plus simple alors est de lancer le script firstboot qui réinitialise OpenWRT.
- Deuxième et dernier recours : si l'opération précédente échoue, il faut réinstaller OpenWRT par TFTP.
En guise de conclusion
- OpenWRT n'apporte guère de fonctionnalités supplémentaires par rapport au firmware d'origine livré par Linksys. Mais - et ce mais est important - il permet l'installation d'outils complémentaires - tels OpenVPN - qui permettent de sécuriser les liaisons Wifi ou augmentent les fonctionnalités offertes, dans la limite des capacités matérielles du routeur. Parmi ces paquetages, citons, outre OpenVPN : antidote (détection de l'ARP Poisoning), arpwatch, etc.
- En outre, OpenWRT est une bonne base d'apprentissage pour qui souhaite construire une AP plus complexe (mais aussi plus onéreuse) par la suite, que ce soit à partir de plate-formes telles que les boitiers Soekris ou même de vulgaires PC sous Linux.
- On attend également avec impatience que des projets comme FreeBSD ou OpenBSD soient portés sur cette plate-forme.